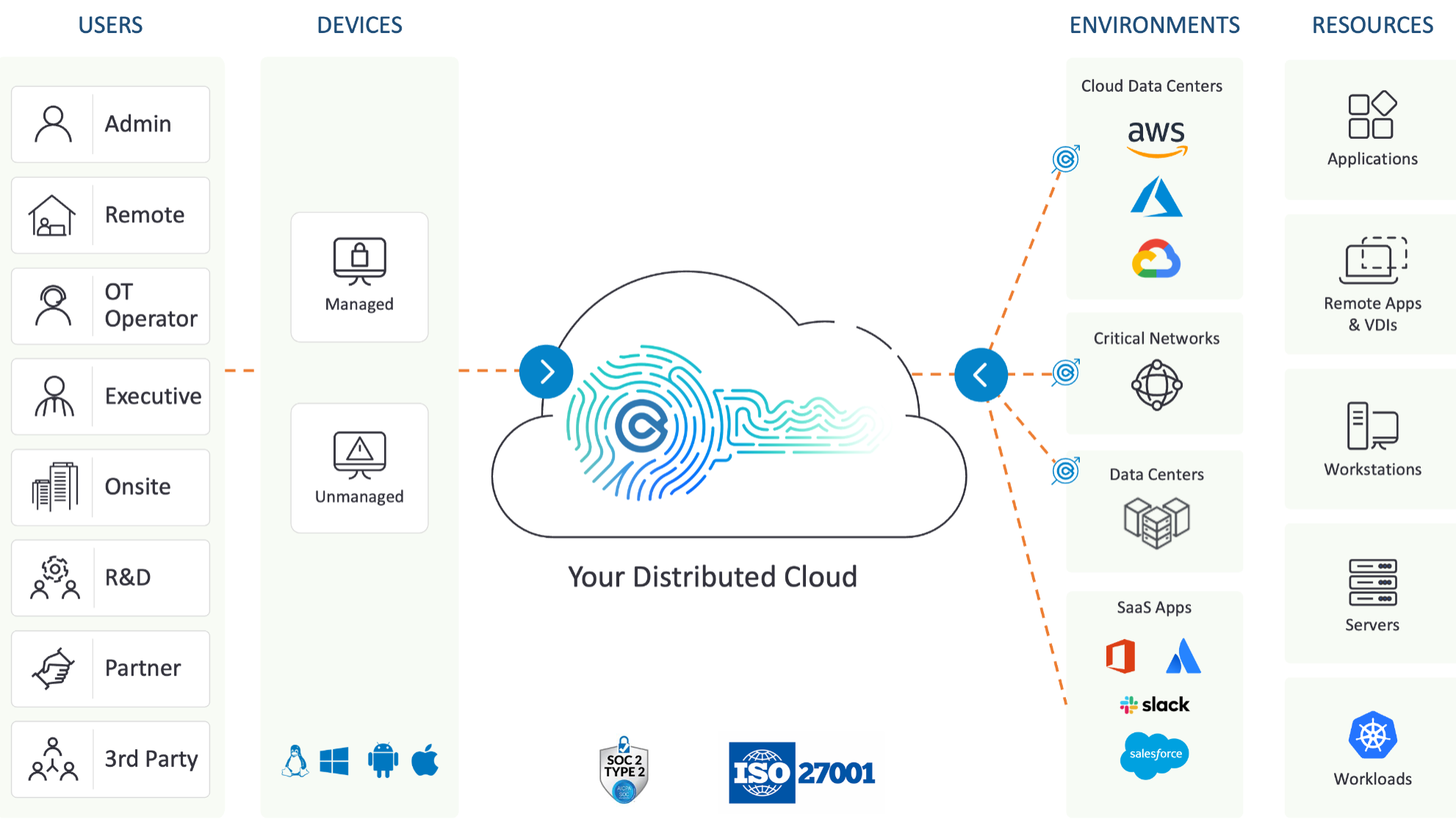
Cyolo retrofits existing systems with modern authentication infrastructure to confidently identify and quickly connect users to the resources they need to do their jobs in today's complex digital environment. After the new infrastructure is installed, the path toward identity-based access and connectivity can be easily taken.
Cyolo helps your organization meet modern compliance and security regulations, extending clould SSO and adaptive MFA to traditional applications, cost-effectively, quickly, and easily. The identity-based access solution works with your existing tech stack and active directory to streamline uniform security policies across all systems, reducing overhead with minimal time to deploy, implement, and enforce IT security.
The platform provides real-time user-to-application access and control with continuous authorization and end-to-end encryption.